What is DNS?
To reach another person on the Internet you have to type an address into your computer - a name or a number. That address has to be unique so computers know where to find each other. ICANN coordinates these unique identifiers across the world. Without that coordination we wouldn't have one global Internet. When typing a name, that name must be first translated into a number by a system before the connection can be established. That system is called the Domain Name System (DNS) and it translates names like www.icann.org into the numbers – called Internet Protocol (IP) addresses. ICANN coordinates the addressing system to ensure all the addresses are unique. (ICANN "DNSSEC-What is it and why is it important?")
According to ICANN, vulnerabilities in the DNS discovered recently allow an attacker to hijack this process of
looking some one up or looking a site up on the Internet using their
name. The purpose of the attack is to take control of the session to,
for example, send the user to the hijacker's own deceptive web site for
account and password collection. Recent posts from various members of the ICT Community Forum on Facebook led me to think that there is a possibility of this happening to company websites. It seems PNG government websites are the prime targets.
Some websites that have been reported on this ICT Community Forum with connectivity issues;
- www.pm.gov.pg
- www.pmnec.gov.pg
- wss.finance.gov.pg
- www.ipa.gov.pg
These and maybe others we are not aware of. There is a possibility that hackers could be intercepting confidential information shared via this websites without ICT even knowing.
I may be entirely wrong in my assumptions as there are also other contributing factors that could be reason as to why certain sites go down without any notice.
Such reasons could be;
- Websites / server hardware undergoing maintenance
- Locally hosted web services migrated to 'cloud' environment. (As is the case with the IPA online services I looked up recently)
- Typically most maintenance work is done offshore with in-house ICT having no to very little control over the whole process.
In one other serious case the site may have been really hacked. As in the case of PNG National Research Institute website recently.
 |
| Figure 1. Typing PNG NRI in Google reveals this. |
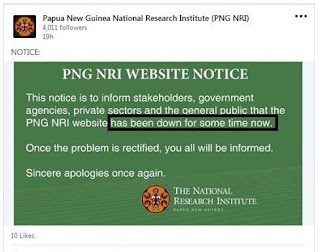 |
| Figure 2. This is what they posted on their FB page. |
Where the vulnerabilities or loopholes in their system are that led to such attacks on their website is a question that begs for an answer. One cannot come to a simple conclusion without having to do a full analysis and audit of their website, network architecture and underlying security firewalls. It will only make matters more difficult or worse if such important websites are hosted offshore with very little support.
Typical web attacks
Nevertheless, vulnerabilities still exist and there are many ways in which web attacks can be launched. According to a presentation by Saumil Shah for BlackHat Asia on the Top Ten Web Attacks, here is a list of the top 10 web hacking techniques;
2. Directory Browsing
3. Retrieving “non-web” Files
4. Reverse Proxying
5. Java Decompilation
6. Source Code Disclosure
7. Input Validation
8. SQL Query Poisoning
9. Session Hijacking
10. Buffer Overflows
Another organization Rapid7 (who are also supporters/sponsors of BlackHat where we get the top list from) lists the following common types of cybersecurity attacks.
- Common Types of Cybersecurity Attacks
- Phishing Attacks
- SQL Injection Attacks (SQLi)
- Cross-Site Scripting (XSS)
- Man-in-the-Middle (MITM) Attacks
- Malware Attacks
- Denial-of-Service Attacks
- Spear Phishing Attacks
- Whaling Phishing Attacks
- Credential Re-use
Almost all the vulnerabilities listed here can and may be closely related to exploitation of vulnerabilities in DNS. Security relies on several layers of protection and there is possibility of a chain reaction of events should a weakness be identified in one layer.
In a recent article by Rene Bakker, he stated that the actual damage or relevance of the abuse of the DNS is hard to determine. There are no reliable figures about the damage done by cybercrime related to the DNS. A clear majority of cybercrime starts with e-mail, but there are a lot of other ways to manipulate the end-user other than by abusing the DNS.
For example, URL Misinterpretation or Manipulation. A URL (Uniform Resource Locator) has the following structure:
| Protocol | Password (optional) | Server name | Port (optional if 80) | Path |
| http:// | user:password@ | www.commentcamarche.net | :80 | /glossair/glossair.php3 |
By manipulating certain parts of a URL, a hacker can get a web server to deliver web pages he is not supposed to have access to. An attacker could modify the server name and redirect users to their own deceptive websites to steal confidential information entered by users of the website.
These vulnerabilities have increased interest in introducing a technology called DNS Security Extensions (DNSSEC) to secure this part of the Internet's infrastructure.
What is DNSSEC?
DNSSEC is a technology that was developed to, among other things, protect against such attacks by digitally 'signing' data so you can be assured it is valid. However, in order to eliminate the vulnerability from the Internet, it must be deployed at each step in the lookup from root zone to final domain name (e.g., www.icann.org). Signing the root (deploying DNSSEC on the root zone) is a necessary step in this overall processii. Importantly it does not encrypt data. It just attests to the validity of the address of the site you visit. (ICANN)
I do not wish to dwell into the details of this as it has already been done in the ICANN website which you can read here.
In summary, the whole idea you should note here is to verify that the address of the website or the website itself you are visiting is the true legitimate website. This functionality is similar to the Authentication service in the IPSec framework. Through the use of Digital signatures in IPSec VPNs we are able to verify the identity of the sender of a message. In DNSSEC signing of the root zone (top level domain) is necessary to verify the original address and name of the website.
I am not saying here that DNSSEC on its own is the total package but it is one key technology that can be used with other security features like IPSEC, STARTTLS, HTTPS, TLS and others which most likely are already in existence in a good robust network environment (for those who take security very seriously). In Rene's article, he further states that domain registers play an important role in deploying DNSSEC. They provide a secured domain name to their customers, the registrants. It is then the customers (owner of the website) responsibility to consult your ISP or webhost provider to enable this functionality. Of course it comes at a cost. His article which can be found here including the sites listed below in the reference section highlights some key security measures that key stakeholders at different levels can implement to ensure a degree of security is provided for the website and its users.
In conclusion, a concerted effort at all levels in an organization is required to minimize the potential threats that may arise in an organization. Ignorance can mean disaster.
In conclusion, a concerted effort at all levels in an organization is required to minimize the potential threats that may arise in an organization. Ignorance can mean disaster.
References:
- Top Ten Web Attacks. Retrieved Wednesday 25th April. https://www.blackhat.com/presentations/bh-asia-02/bh-asia-02-shah.pdf
- Common Types of Cybersecurity Attacks. Retrieved Wednesday 25th April. https://www.rapid7.com/fundamentals/types-of-attacks/
- DNSSEC - What Is It and Why Is It Important? Retrieved Tuesday 24th April. https://www.icann.org/resources/pages/dnssec-qaa-2014-01-29-en
- URL Manipulation Attacks. Retrieved Wednesday 25th April. https://ccm.net/contents/31-url-manipulation-attacks


No comments:
Post a Comment